Over on F-Secure Antivirus Research Weblog the post “Virus That Blocks Itself” contains this text:
“Virus:W32/Ramnit is no stranger to many malware analysts/researchers, as it was in the wild back in 2010.
Other malware researchers have blogged about the technical details of this interesting virus (here and here, for example); however there are still some noteworthy techniques — and an ‘easter egg’ — waiting to be discovered.
One of the interesting techniques is the injection method that Ramnit uses. This differs from the traditional method, in which a virus would create a suspended thread and inject code using a memory writing Windows API function, then resume the suspended thread after the injection is done.
In this case, what makes Ramnit different is that it calls a Windows API function to spawn a new process, either the default web browser process or the Generic Host Process for Win32 Services, also known as svchost.exe. By injecting into this newly spawned process, the code is not easily visible to users and able to bypass the firewall.
Before this happens though, Ramnit installs an inline hook in an undocumented Windows native system service called Ntdll!ZwWriteVirtualMemory. The picture below depicts how this injection works:
The hooked Windows native system service redirects the code execution flow to the module defined in the caller process to perform the code injection routine. The injected code in the new process includes the capability for file infection (Windows executable and HTML files), as well as backdoor and downloader functionalities.
Another noteworthy detail in Ramnit is its ‘easter egg’, found in the DLL that it injects to the processes mentioned above. The code snapshot below should explain everything:
Basically, this easter egg navigates to the registry key and looks for ‘WASAntidot':
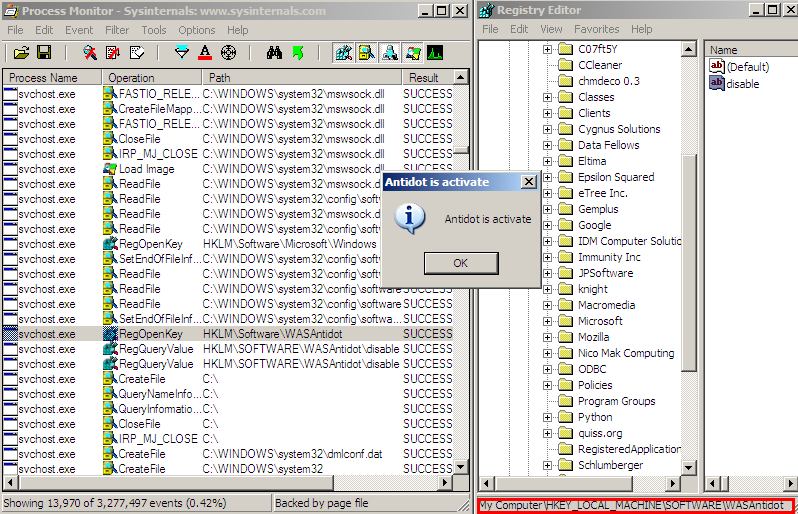
When we try to create ‘WASAntidot’ registry key on a test machine, we see this:
Voila! The machine is safe from Ramnit infection now!
Threat Solutions post by — Wayne
On 08/04/11 At 08:42 AM
“